Table of Contents
Private Endpoints and Service Endpoints
Service Endpoints
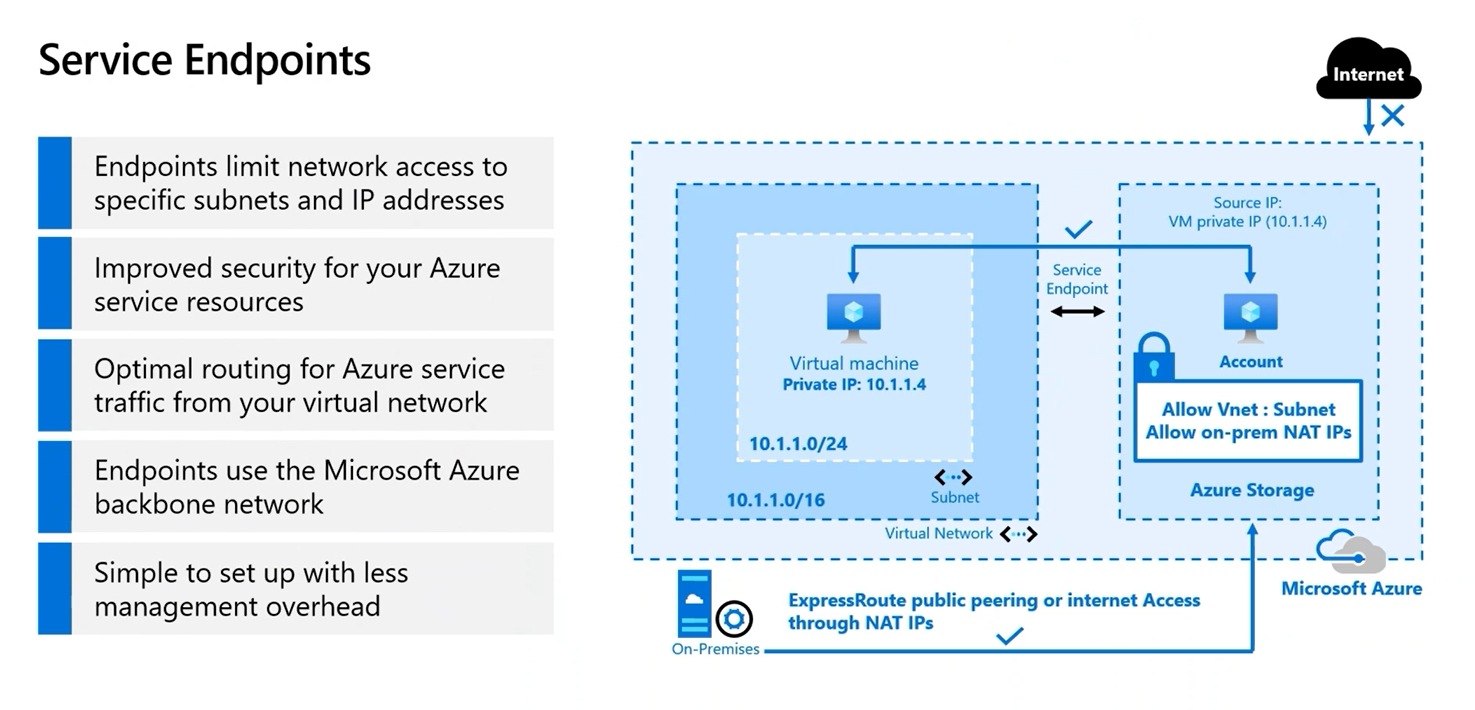
- Service Endpoints allow you to restrict access to your PaaS resources to traffic coming from your Azure Virtual Network. By default many Azure services allow access from the Internet to the service's public endpoint/IP. In many cases this is not needed and it reduces the attack surface to only allow access from select customer networks.
- Service Endpoints makes it so the source IP used by a VM to access public Azure services (e.g. Blob Storage) is a private IP from the VM VNet. The service/target IP is still a public address.
- Be mindful of service firewall rules that are using the public source IPs. Those will need to be adjusted to work for private IPs.
- Service Endpoints are configured per subnet.
- There is no additional cost for Service Endpoints
- When a Forced Tunnel is used the service traffic is exempt from going through the tunnel.
- The Service Endpoint route takes a higher precedence than the default route.
Private Endpoint
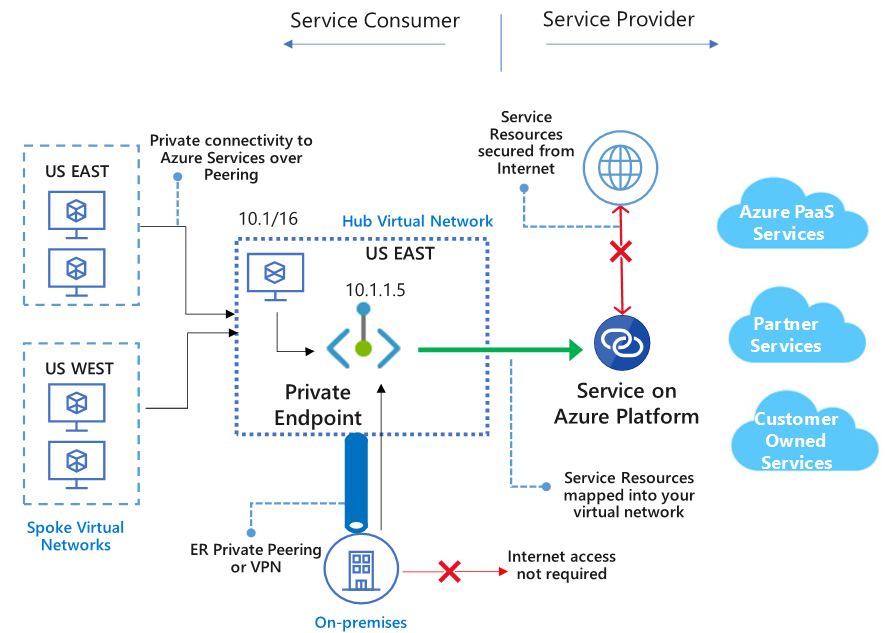
- Private Endpoint allows you to connect your virtual network to services in Azure without a public IP address at the source or destination.
- The key difference between Private Link and Service Endpoints is that with Private Link you are injecting the multi-tenant PaaS resource into your virtual network.
- With Service Endpoints, traffic still leaves your Vnet and hits the public endpoint of the PaaS resource, with Private Link the PaaS resource sits within your Vnet and gets a private IP on your Vnet. When you send traffic to the PaaS resource, it does not leave the virtual network.
§
Forced Tunneling
Forced tunneling lets you redirect or “force” all Internet-bound traffic back to your on-premises location via a Site-to-Site VPN tunnel for inspection and auditing.
This is sometimes referred to as back hauling.