This is an old revision of the document!
Security Operations Management
Configure centralized policy management
- Configure a custom security policy
- Create a policy initiative
- Configure security settings and auditing by using Azure Policy
Configure and manage threat protection
- Configure Microsoft Defender for Servers (not including Microsoft Defender for Endpoint)
- Evaluate vulnerability scans from Microsoft Defender for Servers
- Configure Microsoft Defender for SQL
- Use the Microsoft Threat Modeling Tool
Configure and manage security monitoring solutions
- Create and customize alert rules by using Azure Monitor
- Configure diagnostic logging and log retention by using Azure Monitor
- Monitor security logs by using Azure Monitor
- Create and customize alert rules in Microsoft Sentinel
- Configure connectors in Microsoft Sentinel
- Evaluate alerts and incidents in Microsoft Sentinel
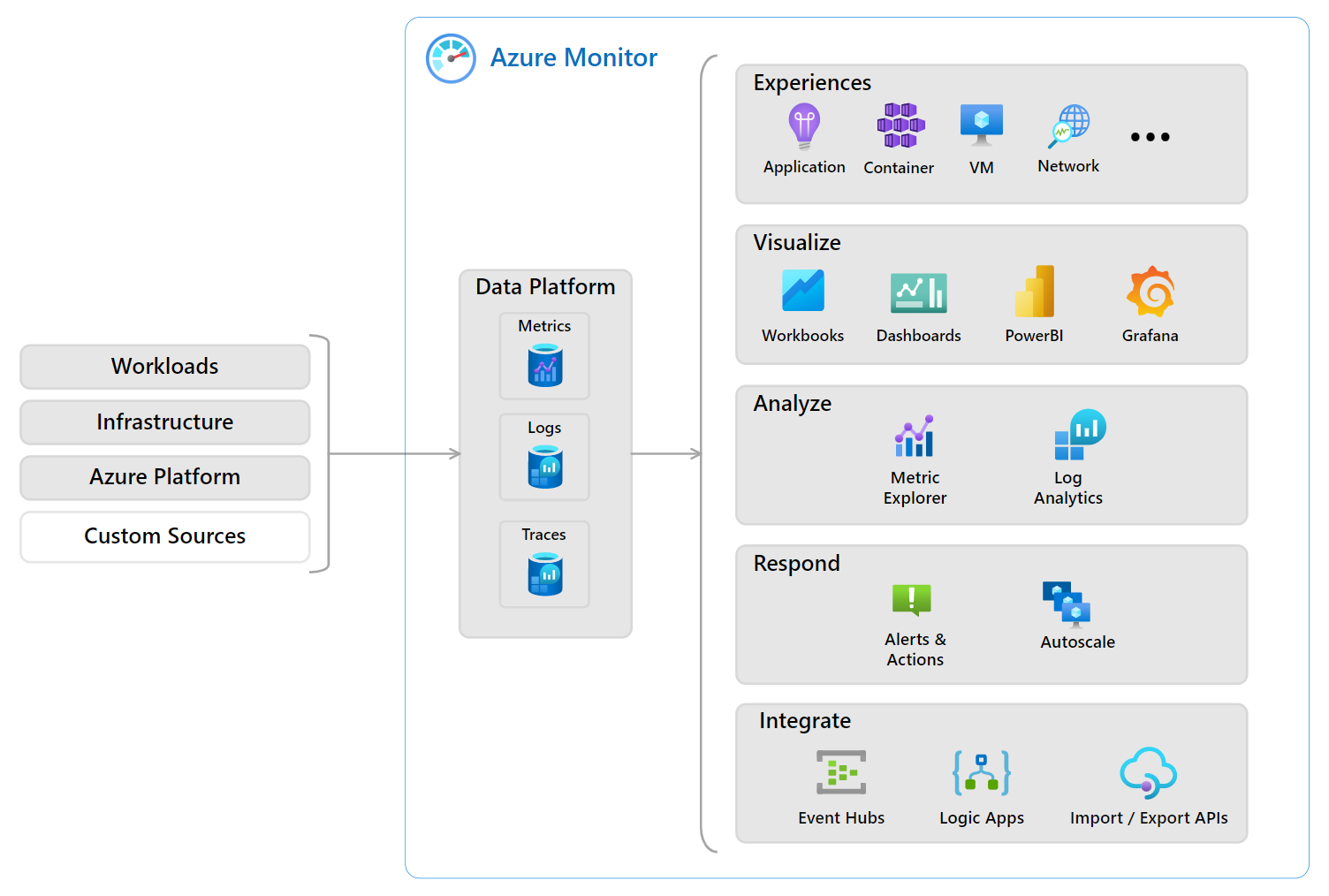
Azure Monitor
Azure Monitor is a service that delivers a comprehensive solution for collecting, analyzing, and acting on telemetry (metrics and logs) from your cloud and on-premises environments.
- Metrics are numeric values collected at regular intervals (e.g. CPU utilization, disk IOPS, network connections, etc.)
- Metrics are produced automatically without any configuration done by the user
- Logs are textual data that are produced organically as things occur in the environment (e.g. user login event)
- Logs are not collected until things are collected until configuration is done by administrators
- Most Azure resources have an option to enable Diagnostic Logs
- Azure Monitoring Agent (AMA) is an agent that runs on Windows or Linux OS that can collect logs and metrics.
- Some logs are automatically generated by resources by default, but for more details logging it maybe necessary to enabled diagnostics logs for a resource, or, in the case of VMs, install an agent on the OS.
Diagnostic Logs vs. Activity Logs
These logs differ from the activity log. The activity log provides insight into the operations, such as creating a VM or deleting a logic app, that Azure Resource Manager performed on resources in your subscription using. The activity log is a subscription-level log. Resource-level diagnostic logs provide insight into operations that were performed within that resource itself, such as getting a secret from a key vault.
- activity logs represent events on the control plane
- diagnostic logs represent events on the data plane
- diagnostic logs may be referred to as resource logs; they represent operations that were performed within a resource
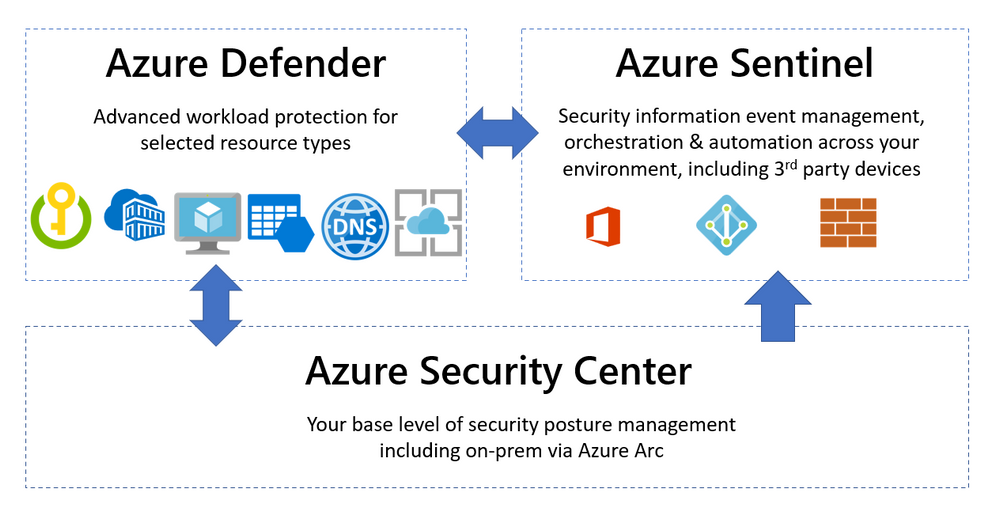
Microsoft Defender for Cloud
Microsoft Defender for Cloud is your central location for setting and monitoring your organizations security posture.
- Microsoft Defender for Cloud was previously known as Azure Security Center.
Microsoft Defender for Cloud is a Cloud Security Posture Management (CSPM) and Cloud Workload Protection Platform (CWPP) for all of your Azure, on-premises, and multi-cloud (Amazon AWS and Google GCP) resources. Defender for Cloud fills three vital needs as you manage the security of your resources and workloads in the cloud and on-premises, continually assess, secure and defend.
- Defender continuously assesses the security posture of environments and their resources and produces a score (based on the Azure Security Benchmark) for it.
- Defender works for Azure, other clouds and on-prem resources.
- JIT VM Access is a feature of Defender that only allows VM access after approval and for a short. fixed amount of time. This mitigates against brute-force types of attacks. (requires the Enhanced Security tier)
- The free tier does not include monitoring non-Azure resources; this requires the Enhance tier of the service.
- Example: Defender would not detect if there is a new version of an OS, but it would detect of there are critical security updates that are missing.
Security Center
Azure Sentinel
- Azure Sentinel is a SIEM/SOAR solution that works off of data from a Log Analytics Workspace
- It ingests data from a variety of source types by using connectors
- There are built-in rules and support for custom rules using the Kusto query language