Role Based Access Control/RBAC
RBAC is an authorization system built on Azure Resource Manager that provides fine-grained access management of Azure resources.
- A security principal is an object that represents a user, group, service principal, or managed identity that is requesting access to Azure resources. You can assign a role to any of these security principals.
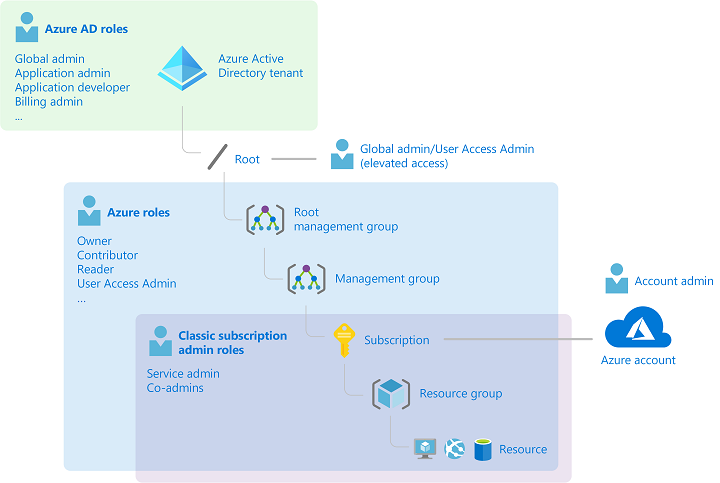
- role scope: RBAC roles can be assigned at the level of management group, subscription, resource group or resource. Roles at higher levels are inherited by lower levels.
- Roles (role definitions) are comprised of scopes and permissions that apply to the scopes.
- The scopes are specified as paths.
- Roles give some identity (user, group, service principle, managed identity) permission to perform some set of actions against some service providers for some defined scope (management group, subscription, resource group).
- Unlike AAD roles ARM roles can be assigned to synced groups in addition to cloud groups and users.
- Custom Roles require a P1 or P2 license
- In RBAC role definitions there are actions and data actions, with the former being actions on the control plane and the later on the data plane. For example, a permission that allows a storage account to be read (as in listing blob containers) is a control plane action, whereas reading the actual blobs is a data plane action.
Azure AD roles vs. Azure Resource Manager (ARM) roles
- AAD Roles vs. ARM/Azure Roles
- AzureAD Roles vs. AzureRM Roles
- Azure directory roles vs. Azure resource roles
Azure AD and Azure resources are secured independently from one another. That is, Azure AD role assignments do not grant access to Azure resources, and Azure role assignments do not grant access to Azure AD. However, if you are a Global Administrator in Azure AD, you can assign yourself access to all Azure subscriptions and management groups in your directory.
- RBAC is generally thought of as being used to apply to the control plane, but it can also be used to apply to data plane operations.
- AAD roles cannot be assigned to regular user groups (by default), but ARM roles can be assigned to regular groups. There is an option that can be enabled for groups to allow AAD roles to be assigned to them.
- Azure AD roles control access to Azure AD resources such as users, groups, and applications using the Microsoft Graph API
- Azure roles control access to Azure resources such as virtual machines or storage using Azure Resource Management
Azure AD Roles
The following are the four fundamental Azure AD administrator roles.
- Global Administrator
- User Administrator
- Helpdesk Administrator
- Billing Administrator
Azure Resource Manager (ARM) Roles
As the name suggests Azure Resource Manager roles are roles that apply to resources within an Azure tenant. Whereas Azure AD roles apply to the tenant itself.
The following are the four fundamental ARM roles.
- Owner
- Contributor
- Reader
- User Access Administrator
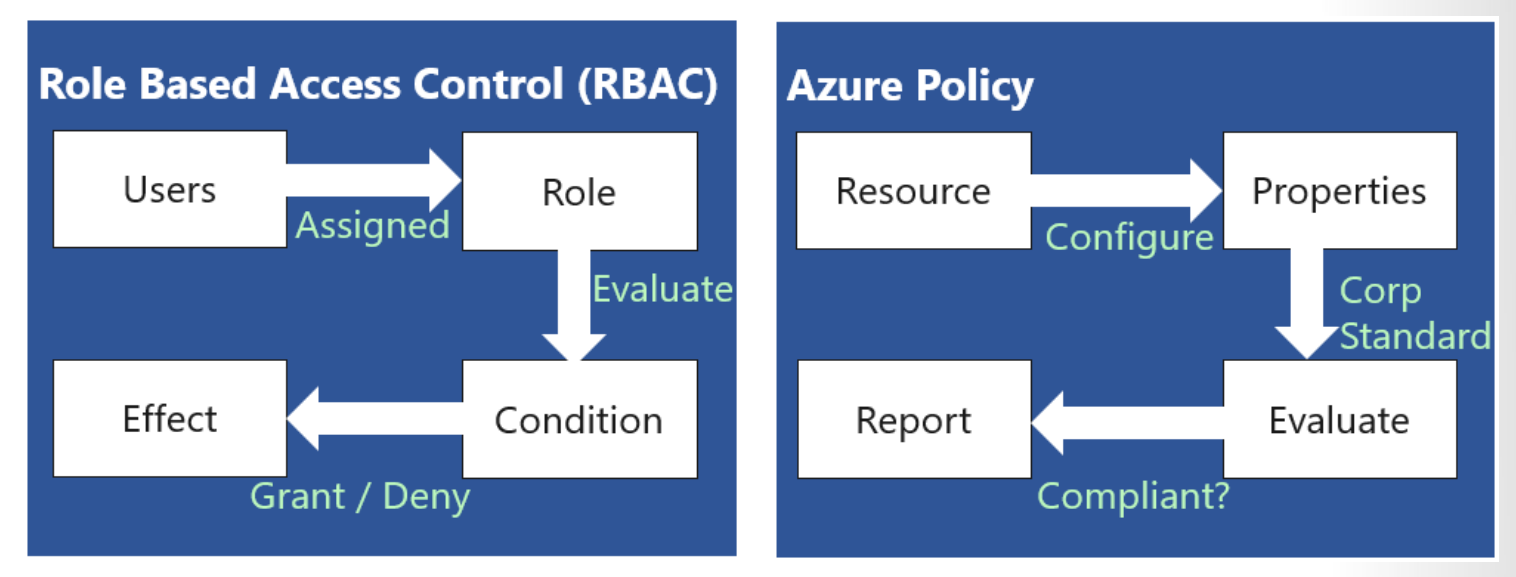
RBAC vs Azure Policies
A few key differences between Azure Policy and RBAC exist. RBAC focuses on user actions at different scopes. You might be added to the contributor role for a resource group, allowing you to make changes to that resource group. Azure Policy focuses on resource properties during deployment and for already-existing resources. Azure Policy controls properties such as the types or locations of resources. Unlike RBAC, Azure Policy is a default-allow-and-explicit-deny system.
Azure Policy focuses on resource properties during deployment and for already-existing resources. Azure Policy controls properties such as the types or locations of resources.
Built-in Roles
| Role | Description |
|---|---|
| Contributor | Lets you manage everything except granting access to resources. |
| Owner | Lets you manage everything, including access to resources. |
| Reader | Lets you view everything, but not make any changes |
| User Access Administrator | Lets you manage user access to Azure resources. |
Access Policies
- In addition to RBAC roles some resources have an additional layer of access control in form of access policies.
- Roles operate at the management plane and access policies operate at the data plane.