Networking
Azure Firewall
- Know the difference between Azure Firewall policies and rules
- policies can be applied to virtual hubs and virtual networks; rules can only be applied to virtual networks
- policies can be centrally managed using Firewall Manager
- rules are managed per firewall
- rules are free
- there are additional costs when policies are applied to more than one firewall
- Know the difference between Azure Firewall and WAF
- virtual hubs vs. virtual network
- firewall rule processing are prioritized in this order…
- network rules
- application rules (target FQDN)
- application rules (FQDN tags), used for Microsoft services
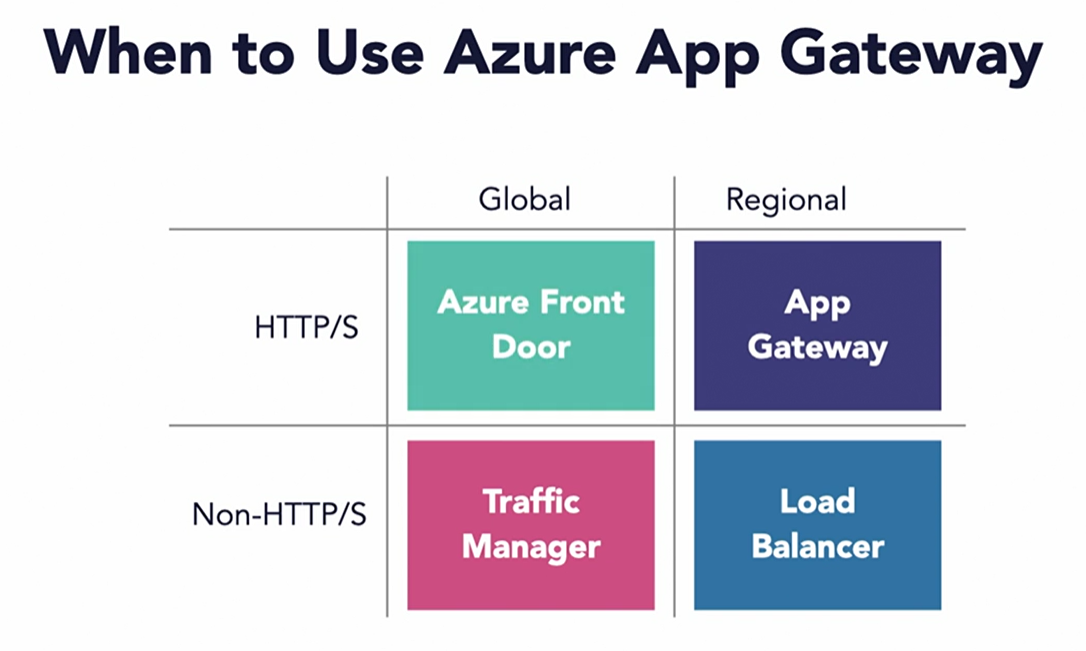
Application Gateway
- An App Gateway combines a L7 load-balancer and WAF
- Logs can be sent to EventHub, Log Analytics or Azure Storage
- Alerts can be sent to Security Center
Resource Firewall
- Is a firewall that can be put in front of certain Azure services (e.g. storage accounts, Azure SQL)
VNet Integrations
- Azure provides VNet integrations for AppServices Apps and Functions
- network restrictions on AppServices and Functions traffic
- User Defined Routes (UDR) are supported to handle routing of traffic
Exam Tip
- Know network security options for App Service, Functions, AKS and storage
Service Endpoints/Private Endpoints
- Service Endpoints limits access to specified VNets for all instances of a PaaS service via the Microsoft backbone network (instead of the internet)
With service endpoints, service traffic switches to use virtual network private addresses as the source IP addresses when accessing the Azure service from a virtual network. This switch allows you to access the services without the need for reserved, public IP addresses used in IP firewalls.
- Private Endpoints (PEs) limits access to specific instances of PaaS services to go over a private network integrated with a customer VNet
- NSGs don't factor into PEs since the resource is mapped to an IP in the VNet.
- PEs include built-in data exfiltration protection
- SEs require the use of network virtual appliance or firewall to get data exfiltration protection
- Private Link is the Azure service provided by various PaaS services that enables Private Endpoints. There can be third-party Private Link services in an addition to the Azure provided ones.
- A Private Endpoint must be deployed in the same region and subscription as the VNet, but the Private Link service can be deployed in a different region and the VNet and PE
- You can enable Private Link for your own apps/services by putting them behind a Azure Load Balancer
Exam Tip
- Know the use cases for Private Endpoints
Encryption in transit
Exam Tip
- Walk through the App Service managed certificate configuration before exam