This is an old revision of the document!
Networking
Azure Firewall
- Know the difference between Azure Firewall policies and rules
- policies can be applied to virtual hubs and virtual networks; rules can only be applied to virtual networks
- policies can be centrally managed using Firewall Manager
- rules are managed per firewall
- rules are free
- there are additional costs when policies are applied to more than one firewall
- Know the difference between Azure Firewall and WAF
- virtual hubs vs. virtual network
- firewall rule processing are prioritized in this order…
- network rules
- application rules (target FQDN)
- application rules (FQDN tags), used for Microsoft services
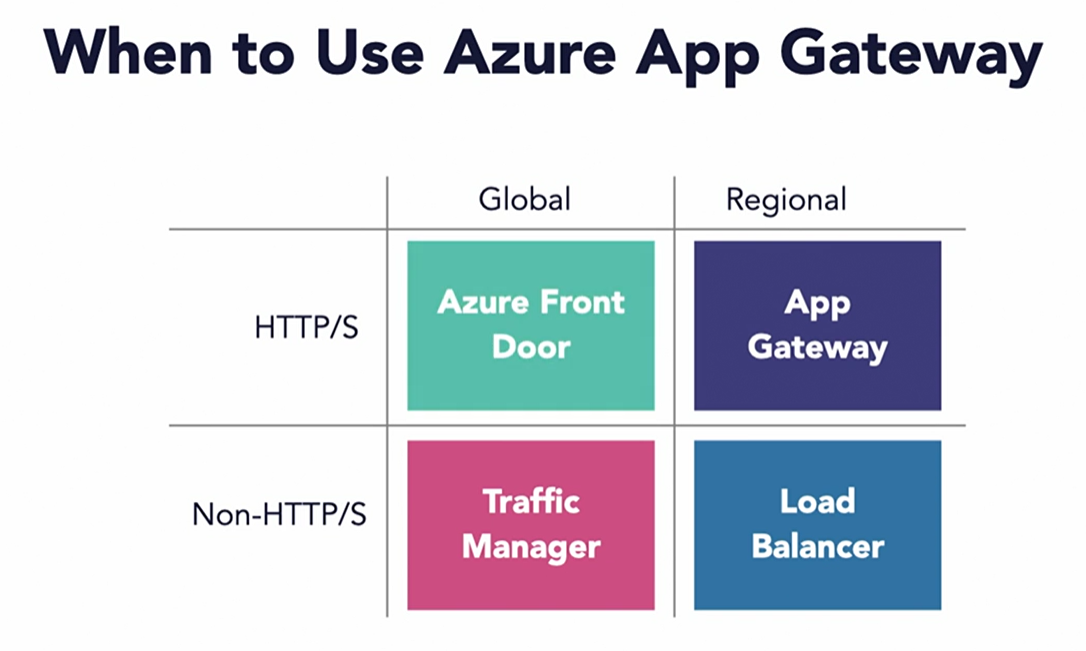
Application Gateway
- An AppGateway combines a L7 load-balancer and WAF
- Logs can be sent to EventHub, Log Analytics or Azure Storage
- Alerts can be sent to Security Center
Resource Firewall
- Is a firewall that can be put in front of certain Azure services (e.g. storage accounts, Azure SQL)
VNet Integrations
- Azure provides VNet integrations for AppServices Apps and Functions
- network restrictions on AppServices and Functions traffic
- User Defined Routes (UDR) are supported to handle routing of traffic
Exam Tip
- Know network security options for App Service, Functions, AKS and storage
Service Endpoints/Private Endpoints
- Service Endpoints limits access to specified VNets for all instances of a PaaS service via the Microsoft backbone network (instead of the internet)
- Private Endpoints (PEs) limits access to specific instances of PaaS services to go over a private network integrated with a customer VNet
- NSGs don't factor into PEs since the resource is mapped to an IP in the VNet.
- PEs include built-in data exfiltration protection
- SEs require the use of network virtual appliance or firewall to get data exfiltration protection