Manage secure access by using Azure AD
- Configure Azure AD Privileged Identity Management (PIM)
- Implement Conditional Access policies, including multifactor authentication
- Implement Azure AD Identity Protection
- Implement passwordless authentication
- Configure access reviews
Privileged Identity Management (PIM)
Identity Protection
- Identity Protection provides policies for a few common scenarios.
- These policies require an AAD P2 license
- These are under
Azure AD/Manage/Security/Identity Protection/Protectand include these:- Azure AD MFA registration policy - requires users to register for MFA
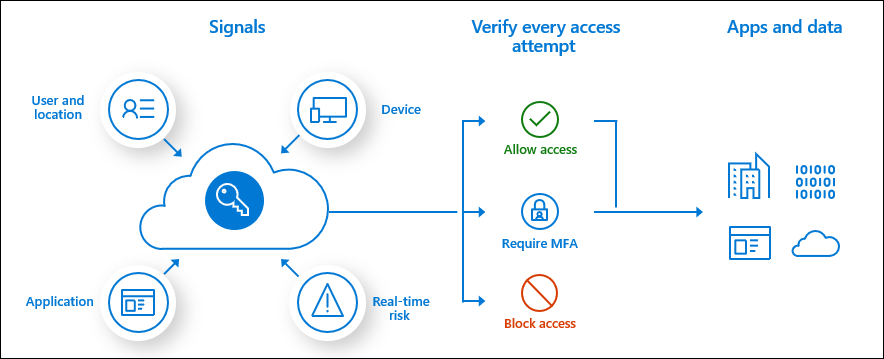
- Sign-in risk policy - a risk score is calculated to indicate the likelihood that a sign-in was not performed by the user. Based on this score administrators can choose to block access, allow access or allow access but require multi-factor authentication.
- User risk policy - a risk score is calculate to indicate the likelihood that a user account has been compromised. Based on this score administrators can choose to block access, allow access or allow access but require a password change.
Identity Protection is a tool that allows organizations to accomplish three key tasks:
- Automate the detection and remediation of identity-based risks.
- Investigate risks using data in the portal.
- Export risk detection data to third-party utilities for further analysis.
- Requires an AAD P2 license
AAD has three Identity Protection policies by default:
- MFA authentication registration policy
- User risk remediation policy
- Sign-in risk policy
The signals generated by and fed to Identity Protection, can be further fed into tools like Conditional Access to make access decisions, or fed back to a security information and event management (SIEM) tool for further investigation based on your organization's enforced policies.
The risk signals can trigger remediation efforts such as requiring users to: perform Azure AD Multi-Factor Authentication, reset their password using self-service password reset, or blocking until an administrator takes action.
User Risk Policy
- User risk is a calculation of probability that an identity has been compromised.
- Administrators can choose to block access, allow access, or allow access but require a password change using Azure AD self-service password reset
Sign-in Risk Policy
- Sign-in risk represents the probability that a given authentication request isn't authorized by the identity owner.
- Identity Protection analyzes signals from each sign-in, both real-time and offline, and calculates a risk score based on the probability that the sign-in wasn't performed by the user. Administrators can decide based on this risk score signal to enforce organizational requirements. Administrators can choose to block access, allow access, or allow access but require multi-factor authentication.
- Sign-in risk is about a particular sign-in event, whereas user risk is about multiple factors, including anomalous sign-ins.
Azure MFA Registration Policy
- As a best practice it is recommended to require MFA and this policy does that.
- MFA Enabled = The admin has enabled MFA on the account, but the user hasn't set it up.
- MFA Enforced = The user has completed the setup of their MFA.
Risk Events
AAD detects the following types of risks. The P2 license gives the most detail info, while the P1 license doesn't include all the details.
- Users with leaked credentials
- Sign-ins from anonymous IP addresses
- Impossible travel to atypical locations
- Sign-ins from infected devices
- Sign-in from unfamiliar locations
- Sign-ins from IP addresses with suspicious activity
Conditional Access
- Conditional Access is a capability that takes in various signals and determines whether a given user should be granted access to resources.
- Conditional Access requires a AAD P1 license, but the risk-based policy capabilties requires a P2 license
- When a user/group is both included and excluded in a policy the exclusion overrides the inclusion.
Azure AD Access Reviews
- Access Reviews refers the features in Azure and process around it to periodically review user access to make sure only the right people have continued access.
- Requires an Azure AD P2 license
- Access Reviews can be use to see who has administrative access, who is a Global Administrator, who is a guest/external user.
- There are multiple types of reviews as shown here, https://docs.microsoft.com/en-us/azure/active-directory/governance/access-reviews-overview#where-do-you-create-reviews
- security/Office 365 groups
- application access
- AAD role
- ARM/RBAC roles
- As part of creating an Access Review you specify things like the frequency of the review and who will do the review.