Platform Protection
Implement advanced network security
- Secure the connectivity of hybrid networks
- Secure the connectivity of virtual networks
- Create and configure Azure Firewall
- Create and configure Azure Firewall Manager
- Create and configure Azure Application Gateway
- Create and configure Azure Front Door
- Create and configure Web Application Firewall (WAF)
- Configure a resource firewall, including storage account, Azure SQL, Azure Key Vault, or Azure
- App Service
- Configure network isolation for Web Apps and Azure Functions
- Implement Azure Service Endpoints
- Implement Azure Private Endpoints, including integrating with other services
- Implement Azure Private Links
- Implement Azure DDoS Protection
Configure advanced security for compute
- Configure Endpoint Protection for virtual machines (VMs)
- Implement and manage security updates for VMs
- Configure security for container services
- Manage access to Azure Container Registry
- Configure security for serverless compute
- Configure security for an Azure App Service
- Configure encryption at rest
- Configure encryption in transit
Perimeter Security
DDoS Protection
- There is a Basic level DDoS protection that is automatic (doesn't require any end-user configuration) and a Standard level that is specifically tuned to VNet resources by the end-user.
- Standard protection does not apply to App Services.
- Standard protection applies to public addresses on resources like, virtual machines, Azure Load Balancers and Application Gateways.
DDoS Protection blocks attack traffic and forwards the remaining traffic to its intended destination. Within a few minutes of attack detection, you’ll be notified with Azure Monitor metrics. By configuring logging on DDoS Protection Standard telemetry, you can write the logs to available options for future analysis. Azure Monitor retains metric data for DDoS Protection Standard for 30 days.
Azure Firewall
- Azure Firewall has built-in high-availability and scalability, so no additional load-balancers are needed.
- Has built-in AZ redundancy capabilities
- Azure Firewall supports three types of rules, NAT, network and application.
- Network rules are applied first then application.
- Rules are terminating, meaning once a matching rule is found for traffic no other matching rules are applied.
- Packets are denied by default.
- By default, there is an implicit network allow rule for DNAT rules.
- Service Tags can be used (for Azure services) in firewall rules in place of IPs for Azure services to simplify things by abstracting away the need to specify IPs.
- FQDN Tags can be used in firewall rules to allow traffic to all FQDNs that are part of the tag.
Premium SKU
- TLS inspection
- IDPS
- URL filtering - extends standard tier FQDN capabilities to handle full URL
- web categories - allows filtering based on categories of website content (e.g. social media, gambling, etc.)
Azure Firewall Manager
- With Azure Firewall Manager you can centrally deploy and configure multiple Azure Firewall instances that span different Azure regions and subscriptions.
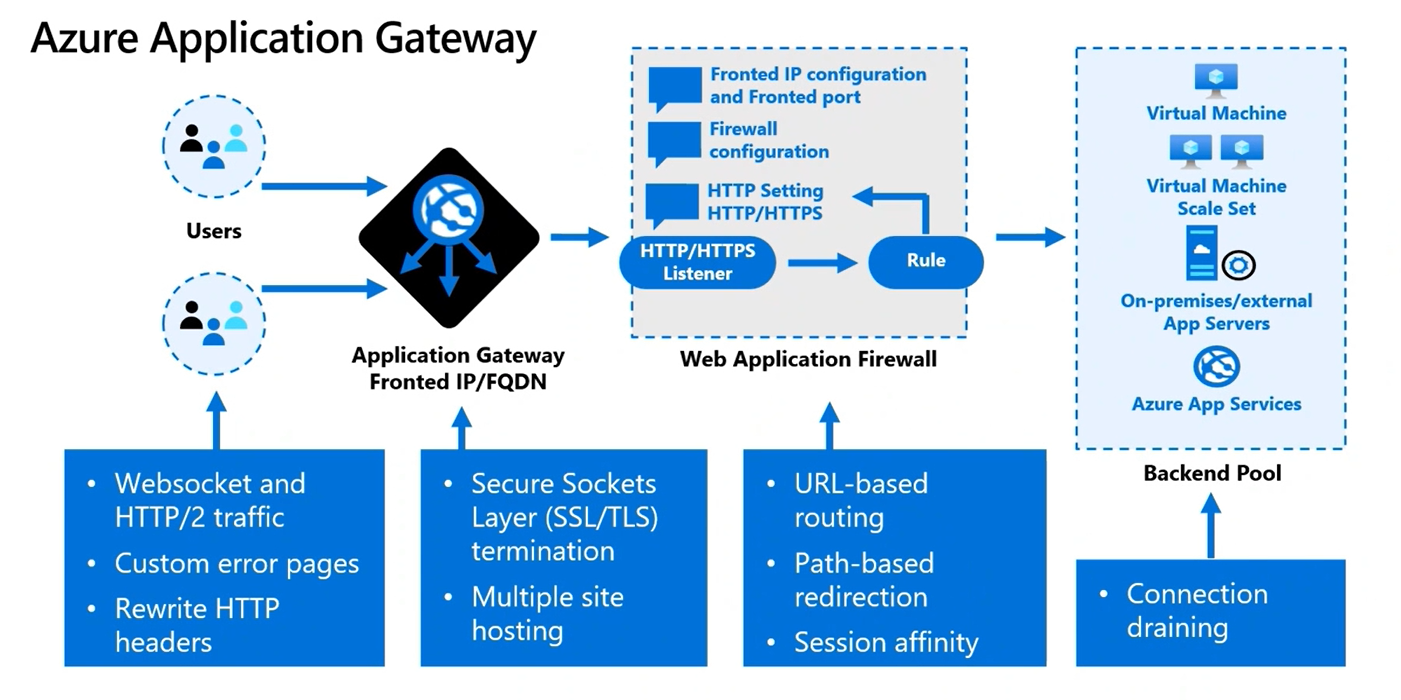
Application Gateway
- Is a layer 7 device
Front Door
- Front Door is a global layer 7 load-balancer service
- The Premium v2 sku supports Private Endpoints for the origin servers
Application Gateway vs Front Door
While both Front Door and Application Gateway are layer 7 (HTTP/HTTPS) load balancers, the primary difference is that Front Door is a non-regional service whereas Application Gateway is a regional service.
Network Security Groups (NSGs)
- NSGs can be applied at the subnet or NIC level
- In addition to inter-subnet traffic NSG rules also effect intra-subnet traffic.
Application Security Groups
- Unlike NSGs, ASGs use references to NICs instead of IP addresses, so the IPs are abstracted away.
Service Endpoints and Private Endpoints
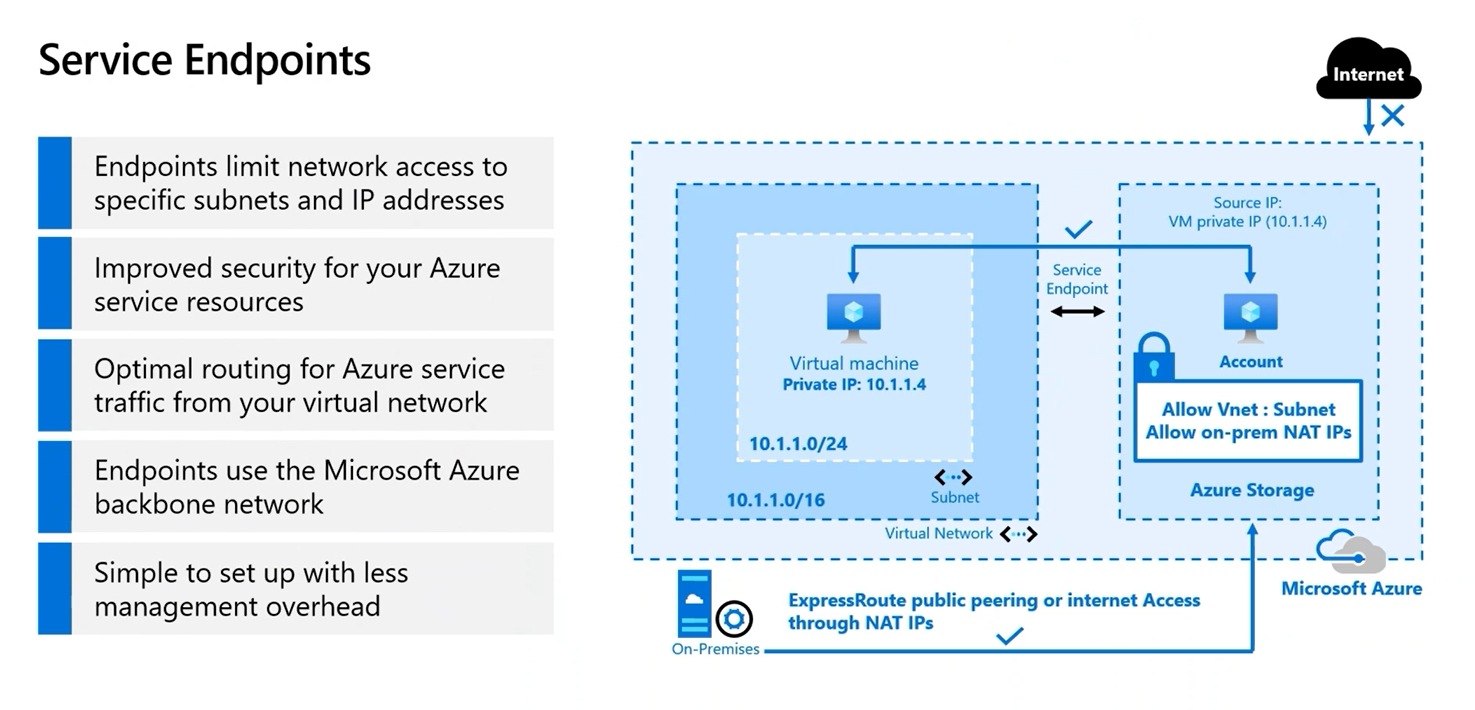
Service Endpoints
- Service Endpoints allow you to restrict access to your PaaS resources to traffic coming from your Azure Virtual Network. By default many Azure services allow access from the Internet to the service's public endpoint/IP. In many cases this is not needed and it reduces the attack surface to only allow access from select customer networks.
- Service Endpoints makes it so the source IP used by a VM to access public Azure services (e.g. Blob Storage) is a private IP from the VM VNet. The service/target IP is still a public address.
- Be mindful of service firewall rules that are using the public source IPs. Those will need to be adjusted to work for private IPs.
- Service Endpoints are configured per subnet.
- There is no additional cost for Service Endpoints
- When a Forced Tunnel is used the service traffic is exempt from going through the tunnel.
- The Service Endpoint route takes a higher precedence than the default route.
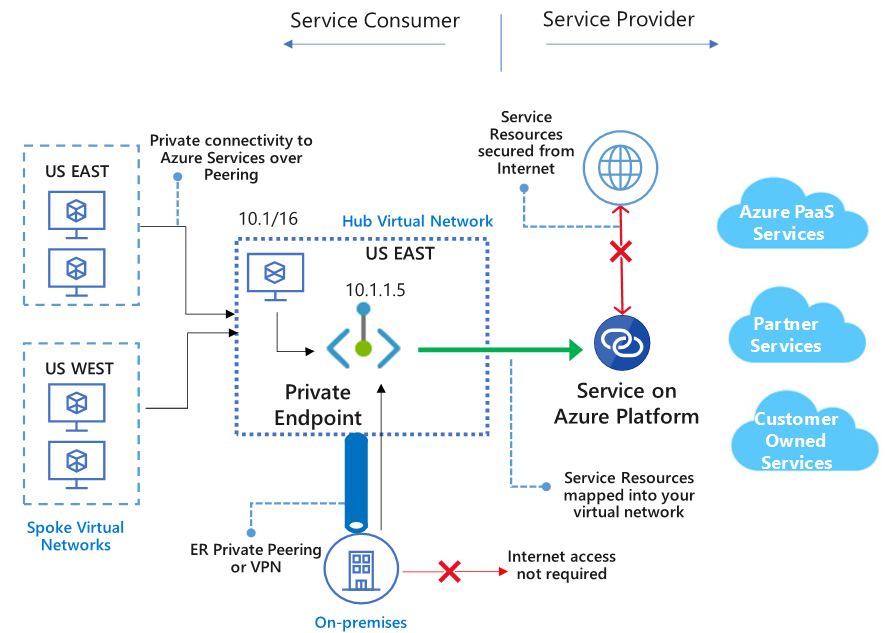
Private Endpoint
- Private Endpoint allows you to connect your virtual network to services in Azure without a public IP address at the source or destination.
- The key difference between Private Link and Service Endpoints is that with Private Link you are injecting the multi-tenant PaaS resource into your virtual network.
- With Service Endpoints, traffic still leaves your Vnet and hits the public endpoint of the PaaS resource, with Private Link the PaaS resource sits within your Vnet and gets a private IP on your Vnet. When you send traffic to the PaaS resource, it does not leave the virtual network.
§
Forced Tunneling
Forced tunneling lets you redirect or “force” all Internet-bound traffic back to your on-premises location via a Site-to-Site VPN tunnel for inspection and auditing.
This is sometimes referred to as back hauling.
Disk Encryption
- Windows uses BitLock for disk encryption
- Linux uses DM-Crypt for disk encryption
- Disks are stored as page blobs in storage accounts
- Customer managed keys can be used and kept in Azure Key Vault
Container Security
- ACR = Azure Container Registry