Azure IAM
- AzureAD vs. AzureRM roles
- Entities that can be granted access to resources in Azure are generally called security principals. This includes users, groups, service principles and managed identities.
Azure Administrator Roles (Entra ID Roles) vs. Azure Roles (Azure RBAC Roles)
- Entra roles/directory (scope) roles, administrator roles
- Azure roles, Azure RBAC roles, Azure resource roles
- There are some built-in roles for Entra ID and Azure that have the same name, for example, Reader and Security Reader.
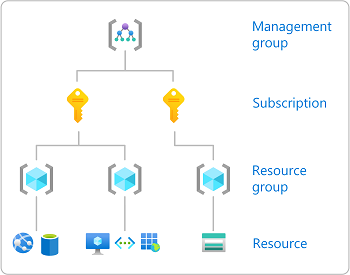
Tenant/Root Managment Group Level Access
- As a Global Admin you may need to enable the option to grant yourself access to management groups/subscriptions in your tenant. Under the tenant Properties screen there is an option (toggle) for this. It allows the user to manage access to all Azure subscriptions and management groups in the tenant.
- This setting adds the role User Access Administrator to the root Management Group, which lets you manage user access to Azure resources.
- ☝️This setting is for special use cases. Most access to resources is controlled by RBAC and assigning specific roles to certain scopes.
- This is referred to as elevated access.
Microsoft Entra ID and Azure resources are secured independently from one another. That is, Microsoft Entra role assignments do not grant access to Azure resources, and Azure role assignments do not grant access to Microsoft Entra ID. However, if you are a Global Administrator in Microsoft Entra ID, you can assign yourself access to all Azure subscriptions and management groups in your directory. Use this capability if you don't have access to Azure subscription resources, such as virtual machines or storage accounts, and you want to use your Global Administrator privilege to gain access to those resources.
RBAC/Roles
- Instead of assigning individual rights to a security principle role-based access control (RBAC) is used to assign rights to a role and then assign roles to users. This level of indirection is more manageable.
- In Azure there are two general types of roles, Azure AD roles and RBAC roles.
- To assign a user, group or service principle a role the scope is specified. The scope can be at the level of Management Group, Subscription, Resource Group, or Resource.
- Control plane actions can have a Management Group scope, but data plane actions cannot. Data plan actions can be at the subscription level.
- Example of a control plane action is,
Microsoft.Storage/storageAccounts/listKeys/action. - Example of a data plane action is,
Microsoft.KeyVault/vaults/keys/get/action
Service Accounts
Microsoft’s guidance is to avoid using regular user accounts as service accounts when possible. Instead:
- Use App Registrations + Service Principals with client secret or certificate auth.
- Use Managed Identities if the service runs in Azure, so you don’t manage credentials at all.
Security Principles
- user
- group
- Service Principle
- Managed Identity
Managed Identity
- What is system managed vs. user managed?
Read-only Access
The following roles/permissions are good for doing security assessments.
- Reader
- Reader and Data Access, allows access to storage account keys, which provides access to various bits of configuration and the contents of the containers.
Microsoft.Network/networkInterfaces/effectiveRouteTable/action, this permission allows the effective routes for a NIC to be listed
Conditional Access
- https://github.com/aollivierre/ConditionalAccess, Baseline Conditional Access Policies
To Explore
- https://idpowertoys.merill.net/, Conditional Access Policy Visualizer
Roles
- User Access Administrator
From CIS Azure Foundations Benchmark:
The User Access Administrator role grants the ability to view all resources and manage access assignments at any subscription or management group level within the tenant. Due to its high privilege level, this role assignment should be removed immediately after completing the necessary changes at the root scope to minimize security risks.
Working With Roles
Get the Azure Roles assigned to a user.
Get-AzRoleAssignment -SigninName "Michael.Gupton@xyz.org" | select RoleDefinitionName, Scope
az role assignment list --assignee "Michael.Gupton@xyz.org"
Get Roles that have a permission
Get-AzRoleDefinition | Where-Object {
$_.Actions -match "Microsoft.Authorization/policyAssignments"
}