§ Manage Azure Active Directory (Azure AD) identities
- Create and manage a managed identity for Azure resources
- Manage Azure AD groups
- Manage Azure AD users
- Manage external identities by using Azure AD
- Manage administrative units
- AAD does not use Kerberos or NTLM like traditional on-prem AD, instead it uses protocols like, OAuth, SAML, OpenID and WS-Federation.
- Best Practice: Limit Global Administrator to 5 or less users in an organization.
- Unlike traditional AD, Azure AD has a flat structure. There are no OUs.
- AAD roles can be assigned to users and to certain groups that have the option enable to allow roles to be assigned to them.
- AAD supports three methods of authentication, native AAD auth, pass-thru auth and federated auth.
- B2B is method of granting access to an external (through a third-party identity provider) user principle.
- Authentication is handled by the third-party provider and authorization is handled by the AAD that is granting access.
Users & Groups
- There are two group types in AAD
- Security groups - Azure AD Security Groups are analogous to Security Groups in on-prem Windows Active Directory. They are Security Principals, which means they can be used to secure objects in Azure AD.
- Microsoft 365 groups - are a membership object in Microsoft 365 that eases the task of ensuring a group of people have consistent permissions to a group of related resources.
- The group's files are in SharePoint, the real time collaboration is in Teams, the email discussions are in Exchange, but they're all secured and managed as a Microsoft 365 Group.
- used for collaboration
Managed Identity
- A Managed Identity is a way for a compute resource (e.g. VM, logic app, app service, function, etc) get access to credentials/security principle without dealing with storing them. This eliminates the problem with having credentials stored in a config file somewhere that could be compromised.
- There are system assigned managed identities and user assigned managed identities.
- With system assigned managed identity there is a one-to-one relationship between a resource that needs a security principle and the security principle.
- With a user assigned managed identity multiple resources (e.g. VMs in scale-set) can share a single security principle.
- A Managed Identity is a way of avoid embedding credentials in application code.
- This allows services, like virtual machines and app service web apps to acquire a token that is subsequently used to get a secret from key vault. And in turn access some resource using the secret.
External Identities
- External Identities includes B2B Collaboration, B2B direct connect and Azure AD B2C.
B2B Collaboration
- B2B collaboration users are managed in the same directory as employees but are typically annotated as guest users.
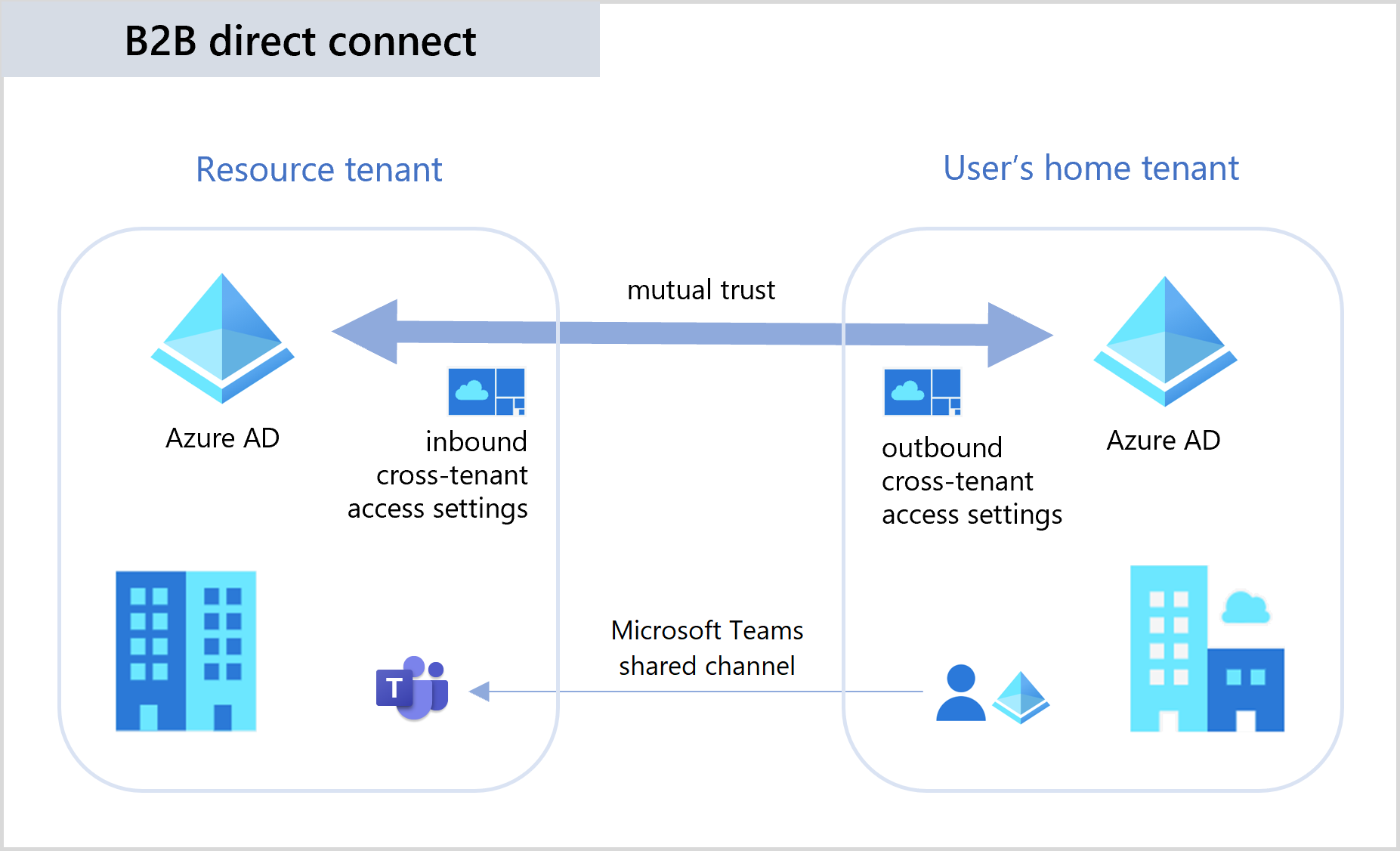
B2B direct connect
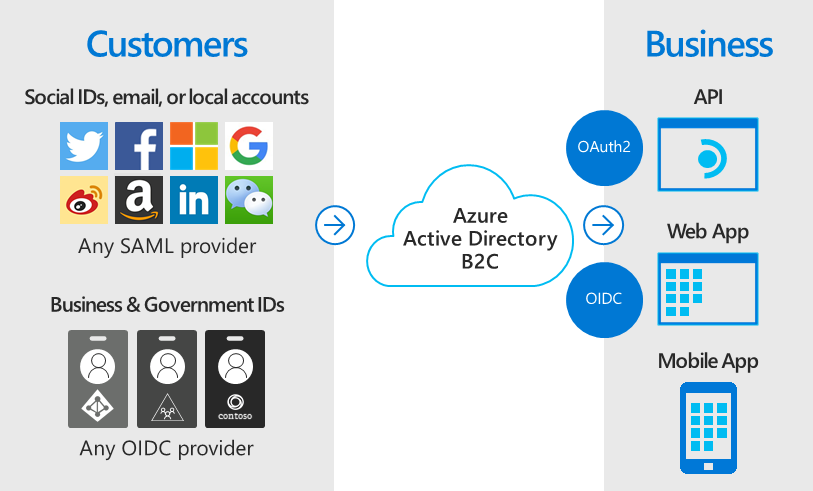
B2C
Azure Active Directory B2C provides business-to-customer identity as a service. Your customers use their preferred social, enterprise, or local account identities to get single sign-on access to your applications and APIs.
Administrative Unit
- An Administrative Unit (AU) is a mechanism for limiting the permissions of an Azure AD role to apply to a selected set of users and/or groups instead of an entire AAD directory. It limits the scope of the role. When a group is selected the scope only applies to the group itself, not the users that are a member of the group.
An administrative unit is an Azure AD resource that can be a container for other Azure AD resources. An administrative unit can contain only users, groups, or devices.
- An administrative unit is similar in some ways to an organization unit in traditional AD.
- A AAD P1 license or better is required for each AU administrator, but members can be AAD free license or better.
- To create an Administrative Unit the user must be a Global Administrator or Privileged Role Administrator.