This is an old revision of the document!
Identity & Access Management
Identity Protection
- Identity Protection provides policies for a few common scenarios.
- These policies require an AAD P2 license
- These are under
Azure AD/Manage/Security/Identity Protection/Protectand include these:- Azure AD MFA registration policy - requires users to register for MFA
- Sign-in risk policy - a risk score is calculated to indicate the likelihood that a sign-in was not performed by the user. Based on this score administrators can choose to block access, allow access or allow access but require multi-factor authentication.
- User risk policy - a risk score is calculate to indicate the likelihood that a user account has been compromised. Based on this score administrators can choose to block access, allow access or allow access but require a password change.
§
Role Based Access Control (RBAC)/Roles
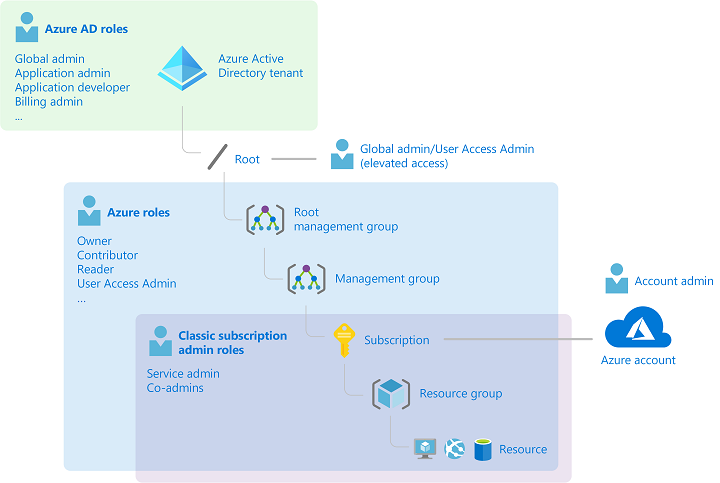
Azure AD roles vs. Azure Resource Manager (ARM) roles
- AAD Roles vs. ARM Roles
Azure AD and Azure resources are secured independently from one another. That is, Azure AD role assignments do not grant access to Azure resources, and Azure role assignments do not grant access to Azure AD. However, if you are a Global Administrator in Azure AD, you can assign yourself access to all Azure subscriptions and management groups in your directory.
- RBAC is generally thought of as being used to apply to the control plane, but it can also be used to apply to data plane operations.
Azure AD Roles
The following are the four fundamental Azure AD administrator roles.
- Global Administrator
- User Administrator
- Helpdesk Administrator
- Billing Administrator